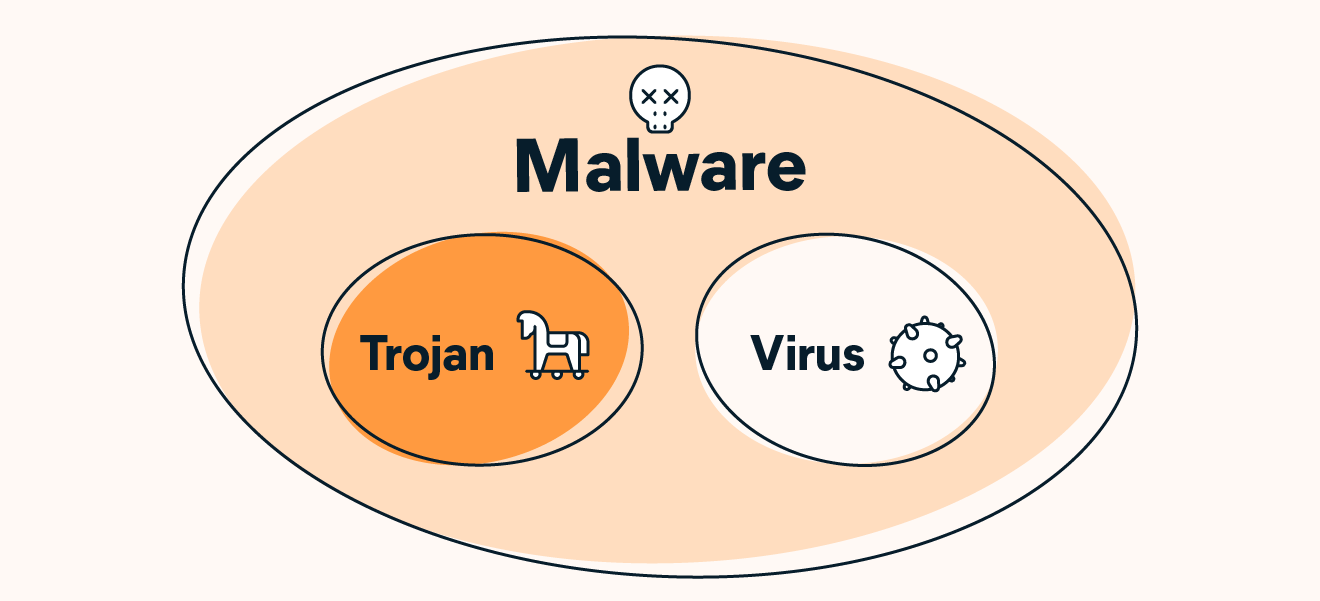
Trojan horse virus attack top
Trojan horse virus attack top, Trojan Attacks How Does Trojan Horse Infect Devices top
$90.00
SAVE 50% OFF
$45.00
$0 today, followed by 3 monthly payments of $15.00, interest free. Read More
Trojan horse virus attack top
Trojan Attacks How Does Trojan Horse Infect Devices
What Is a Trojan a Virus or Malware How Does It Work Avast
What Is a Trojan a Virus or Malware How Does It Work Avast
How to Tell if Your Computer Is Infected by a Trojan Horse
Trojan Virus Images Browse 59 870 Stock Photos Vectors and
Trojan Horse CyberHoot Cyber Library
Description
Product code: Trojan horse virus attack top
What is a Trojan Virus Trojan Horse Malware Imperva top, What is a Trojan Horse Virus Types Prevention in 2024 top, What is a Trojan Horse Virus Types and How to Remove it top, What is a Trojan Horse Virus Types Prevention in 2024 top, What is a Trojan Horse Virus Attack Littlefish Guide top, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus top, What is a Trojan horse attack Shiksha Online top, What is a Trojan Horse U.S. News top, Trojan Horse Meaning Examples Prevention top, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses top, 7 Phases Of A Trojan Horse Attack top, Trojan Horse Meaning Examples Prevention top, What is a Trojan How this tricky malware works CSO Online top, What is a Trojan Horse Virus Definition Examples Removal Options Video top, Unveiling the Trojan Horse A Deceptive Intruder by Faraz top, What is Trojan Horse Computing zenarmor top, Trojan Attacks How Does Trojan Horse Infect Devices top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What Is a Trojan a Virus or Malware How Does It Work Avast top, How to Tell if Your Computer Is Infected by a Trojan Horse top, Trojan Virus Images Browse 59 870 Stock Photos Vectors and top, Trojan Horse CyberHoot Cyber Library top, What is a Trojan Prevention Removal Bitdefender top, Trojan Horse Virus Examples How to Defend Yourself top, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet top, Trojan horse virus hi res stock photography and images Alamy top, Trojan Virus Vector Symbol With Laptop And Red Trojan Horse Stock top, REVE Antivirus Virus protection Antivirus Email Security top, Trojan horse virus hi res stock photography and images Alamy top, Remove Trojan horse virus from Mac MacSecurity top, The Difference Between a Computer Virus Worm Trojan Horse top, CCNA Security Worm Virus and Trojan Horse Attacks top, What Is a Trojan Horse What Are Common Types of Trojan Horse top, What is a Trojan horse attack Shiksha Online top, Aussie Teenager s Spyware Hacked Into Domestic Violence Victims top.
What is a Trojan Virus Trojan Horse Malware Imperva top, What is a Trojan Horse Virus Types Prevention in 2024 top, What is a Trojan Horse Virus Types and How to Remove it top, What is a Trojan Horse Virus Types Prevention in 2024 top, What is a Trojan Horse Virus Attack Littlefish Guide top, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus top, What is a Trojan horse attack Shiksha Online top, What is a Trojan Horse U.S. News top, Trojan Horse Meaning Examples Prevention top, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses top, 7 Phases Of A Trojan Horse Attack top, Trojan Horse Meaning Examples Prevention top, What is a Trojan How this tricky malware works CSO Online top, What is a Trojan Horse Virus Definition Examples Removal Options Video top, Unveiling the Trojan Horse A Deceptive Intruder by Faraz top, What is Trojan Horse Computing zenarmor top, Trojan Attacks How Does Trojan Horse Infect Devices top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What Is a Trojan a Virus or Malware How Does It Work Avast top, How to Tell if Your Computer Is Infected by a Trojan Horse top, Trojan Virus Images Browse 59 870 Stock Photos Vectors and top, Trojan Horse CyberHoot Cyber Library top, What is a Trojan Prevention Removal Bitdefender top, Trojan Horse Virus Examples How to Defend Yourself top, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet top, Trojan horse virus hi res stock photography and images Alamy top, Trojan Virus Vector Symbol With Laptop And Red Trojan Horse Stock top, REVE Antivirus Virus protection Antivirus Email Security top, Trojan horse virus hi res stock photography and images Alamy top, Remove Trojan horse virus from Mac MacSecurity top, The Difference Between a Computer Virus Worm Trojan Horse top, CCNA Security Worm Virus and Trojan Horse Attacks top, What Is a Trojan Horse What Are Common Types of Trojan Horse top, What is a Trojan horse attack Shiksha Online top, Aussie Teenager s Spyware Hacked Into Domestic Violence Victims top.