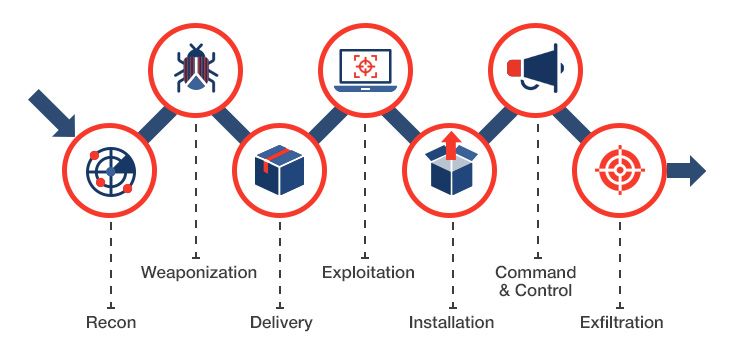
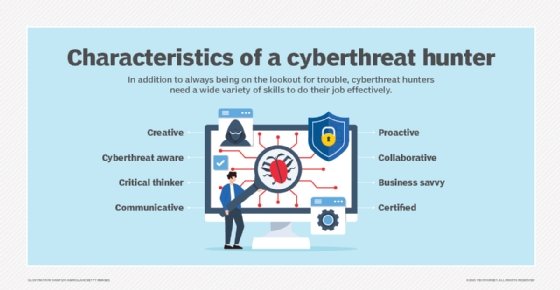
Threat hunting top
Threat hunting top, What is Threat Hunting and how it can benefit your organisation top
$86.00
SAVE 50% OFF
$43.00
$0 today, followed by 3 monthly payments of $14.33, interest free. Read More
Threat hunting top
What is Threat Hunting and how it can benefit your organisation
Threat Hunting
cyber threat hunter cybersecurity threat analyst
What Is Threat Hunting Steps and Advice Cisco
Cyber Threat Hunting and Its Key Elements CERTStation Blog
What is Cyber Threat Hunting Proactive Guide CrowdStrike
Description
Product code: Threat hunting top
What is Cyber Threat Hunting Proactive Guide CrowdStrike top, Threat Hunting. Threat hunting is a proactive cyber by Ey p top, InfoSec s Top 10 Threat Hunting Tools for 2023 Skyhawk top, Threat Hunting Endpoint Network Application Threat Analytics top, Threat Hunting Process Methodologies Tools And Tips top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, What is Threat Hunting Threat Hunting Types and Techniques top, What is threat hunting CyberProof top, Threat Hunting Report Crowd Research Partners top, The Strategy Guide to Threat Hunting Securonix top, How to Mature Your Threat Hunting Program BankInfoSecurity top, Threat Hunting Process from Scratch Download Scientific Diagram top, Threat Hunting Vs. Threat Intelligence InfosecTrain top, What is Threat Hunting CyberRes SME Submission top, How Does Cyber Threat Hunting Work BankInfoSecurity top, What is Cyber Threat Hunting How it works OpenText top, What is Threat Hunting and how it can benefit your organisation top, Threat Hunting top, cyber threat hunter cybersecurity threat analyst top, What Is Threat Hunting Steps and Advice Cisco top, Cyber Threat Hunting and Its Key Elements CERTStation Blog top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, Cyber Threat Hunting What You Need to Know top, What Is Threat Hunting Everything You Want to Know IP With Ease top, The Hunting Loop. Cyber threat hunting is a relatively by Sqrrl top, The Threat Hunting Guide Everything To Know About Hunting Cyber top, Threat Hunting Techniques A Quick Guide top, Threat Hunting. Basic Concepts ClearNetwork Inc top, What is Threat Hunting Sysdig top, Threat hunting Archives Enov8 Solutions top, 5 Step Cyber Threat Hunting Process top, 3 Ways Threat Hunting Improves Security Operations Deepwatch top, A Threat Hunt tale top, Threat Hunting Techniques A Quick Guide top, Threat Hunting Cycle Download Scientific Diagram top.
What is Cyber Threat Hunting Proactive Guide CrowdStrike top, Threat Hunting. Threat hunting is a proactive cyber by Ey p top, InfoSec s Top 10 Threat Hunting Tools for 2023 Skyhawk top, Threat Hunting Endpoint Network Application Threat Analytics top, Threat Hunting Process Methodologies Tools And Tips top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, What is Threat Hunting Threat Hunting Types and Techniques top, What is threat hunting CyberProof top, Threat Hunting Report Crowd Research Partners top, The Strategy Guide to Threat Hunting Securonix top, How to Mature Your Threat Hunting Program BankInfoSecurity top, Threat Hunting Process from Scratch Download Scientific Diagram top, Threat Hunting Vs. Threat Intelligence InfosecTrain top, What is Threat Hunting CyberRes SME Submission top, How Does Cyber Threat Hunting Work BankInfoSecurity top, What is Cyber Threat Hunting How it works OpenText top, What is Threat Hunting and how it can benefit your organisation top, Threat Hunting top, cyber threat hunter cybersecurity threat analyst top, What Is Threat Hunting Steps and Advice Cisco top, Cyber Threat Hunting and Its Key Elements CERTStation Blog top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, Cyber Threat Hunting What You Need to Know top, What Is Threat Hunting Everything You Want to Know IP With Ease top, The Hunting Loop. Cyber threat hunting is a relatively by Sqrrl top, The Threat Hunting Guide Everything To Know About Hunting Cyber top, Threat Hunting Techniques A Quick Guide top, Threat Hunting. Basic Concepts ClearNetwork Inc top, What is Threat Hunting Sysdig top, Threat hunting Archives Enov8 Solutions top, 5 Step Cyber Threat Hunting Process top, 3 Ways Threat Hunting Improves Security Operations Deepwatch top, A Threat Hunt tale top, Threat Hunting Techniques A Quick Guide top, Threat Hunting Cycle Download Scientific Diagram top.