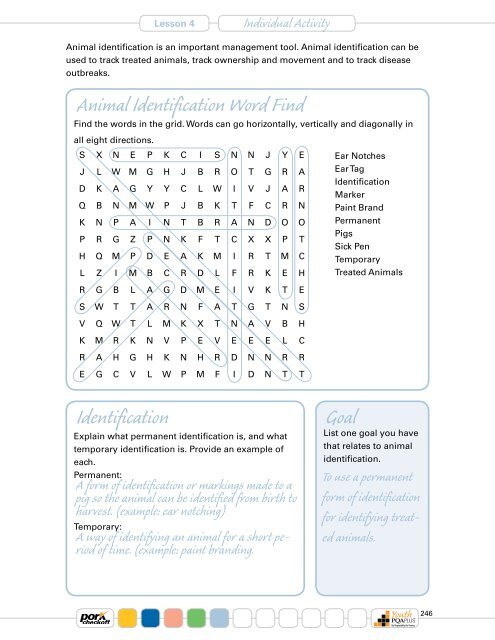
Identification example top
Identification example top, B. Identification Test Directions Select letter of the term from top
$76.00
SAVE 50% OFF
$38.00
$0 today, followed by 3 monthly payments of $12.67, interest free. Read More
Identification example top
B. Identification Test Directions Select letter of the term from
Projective Identification It s Meaning Process and How to deal
Individual Activity
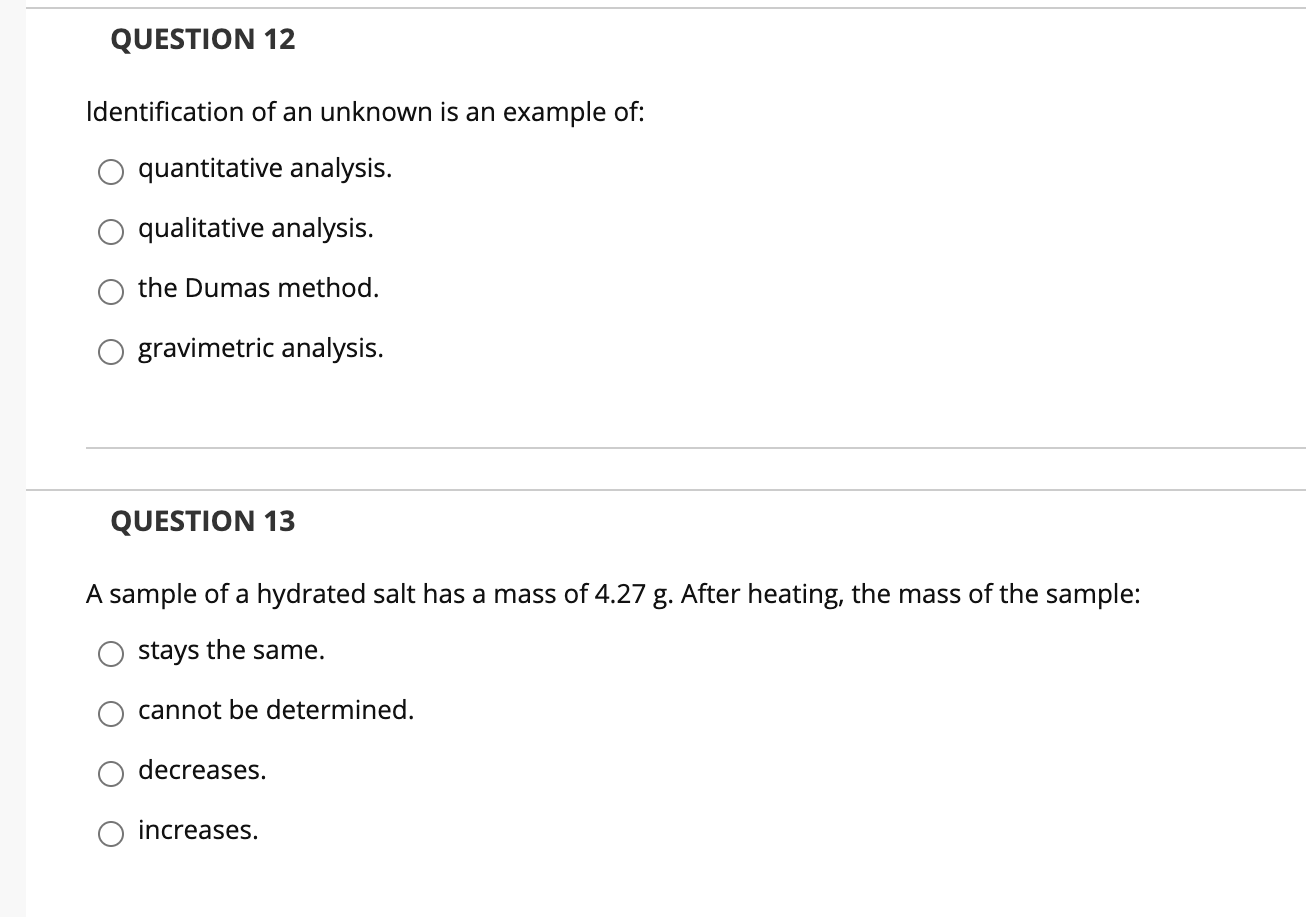
Solved PLEASE HELP ME ANSWER ALL THESE QUESTIONS CORRECTLY
Solved Kindly explain and answer. MODIFIED IDENTIFICATION
VALUE IDENTIFICATION. Value should be a measurement of the by
Description
Product code: Identification example top
8 Examples of Social Identity Race Class and Gender 2024 top, 65 Personal Identity Examples 2024 top, An example of property identification of the question top, Example of a task identification Download Scientific Diagram top, ACTIVITY I IDENTIFICATION TEST Directions Identity what is being top, 1. Examples of studies investigation the link between top, Solved II. Identification provide the term name or phrase top, 22 Aspects of Identity 2024 top, Identification and Completion Type of Test PDF Statistics Data top, Example Asset Identification Cards ENISA top, An example of key diagnostic signs for identification of targeted top, Problem Identification for improving outcomes in healthcare top, JAIC 1987 Volume 26 Number 1 Article 3 pp. 27 to 44 top, Data Identification top, Research problem identification PPT top, Examples of Claims of Organizational Identity Download Table top, B. Identification Test Directions Select letter of the term from top, Projective Identification It s Meaning Process and How to deal top, Individual Activity top, Solved PLEASE HELP ME ANSWER ALL THESE QUESTIONS CORRECTLY top, Solved Kindly explain and answer. MODIFIED IDENTIFICATION top, VALUE IDENTIFICATION. Value should be a measurement of the by top, Demystifying De identification Private AI top, Sample Identification and QC Seq It GmbH top, Written Work A. IDENTIFICATION Identify The Terms Being Described top, 10 Examples of Identification Cards top, 30 Examples of Identity Simplicable top, Identification Code an overview ScienceDirect Topics top, Risk Identification Example Ppt PowerPoint Presentation Styles top, Personal Identification Number PIN What It Is How It s Used top, Successful examples of brand identity important assets Stripo top, Personal identity including for example identifying as black top, PDF A Sociopsychological Conception of Collective Identity The top, Drug target identification using network analysis Taking active top, What are identification and authentication in information security top.
8 Examples of Social Identity Race Class and Gender 2024 top, 65 Personal Identity Examples 2024 top, An example of property identification of the question top, Example of a task identification Download Scientific Diagram top, ACTIVITY I IDENTIFICATION TEST Directions Identity what is being top, 1. Examples of studies investigation the link between top, Solved II. Identification provide the term name or phrase top, 22 Aspects of Identity 2024 top, Identification and Completion Type of Test PDF Statistics Data top, Example Asset Identification Cards ENISA top, An example of key diagnostic signs for identification of targeted top, Problem Identification for improving outcomes in healthcare top, JAIC 1987 Volume 26 Number 1 Article 3 pp. 27 to 44 top, Data Identification top, Research problem identification PPT top, Examples of Claims of Organizational Identity Download Table top, B. Identification Test Directions Select letter of the term from top, Projective Identification It s Meaning Process and How to deal top, Individual Activity top, Solved PLEASE HELP ME ANSWER ALL THESE QUESTIONS CORRECTLY top, Solved Kindly explain and answer. MODIFIED IDENTIFICATION top, VALUE IDENTIFICATION. Value should be a measurement of the by top, Demystifying De identification Private AI top, Sample Identification and QC Seq It GmbH top, Written Work A. IDENTIFICATION Identify The Terms Being Described top, 10 Examples of Identification Cards top, 30 Examples of Identity Simplicable top, Identification Code an overview ScienceDirect Topics top, Risk Identification Example Ppt PowerPoint Presentation Styles top, Personal Identification Number PIN What It Is How It s Used top, Successful examples of brand identity important assets Stripo top, Personal identity including for example identifying as black top, PDF A Sociopsychological Conception of Collective Identity The top, Drug target identification using network analysis Taking active top, What are identification and authentication in information security top.